Release 5.6.0 17 May 2025
This release includes the following new features, enhancements, translations and bugfixes:
KeyStore Password Manager
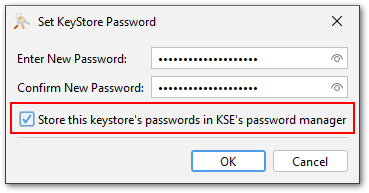
The KeyStore password manager is a new feature that allows to store and manage passwords for keystore files. In combination with the new password generator it is now very easy to create and open keystores without having to type long passwords.
The password manager can be used by selecting the checkbox "Store this keystore's passwords in KSE's password manager" when creating a new keystore or opening an existing one. This decision is on a per-keystore basis and it includes all passwords of this keystore, but it can be changed later.
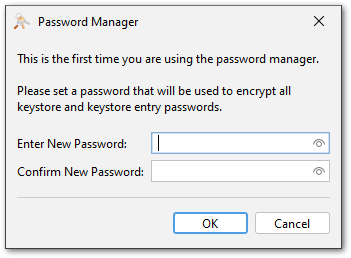
On the first use of the password manager, a global password for the password manager must be set. This password is used to encrypt the passwords stored in the password manager.
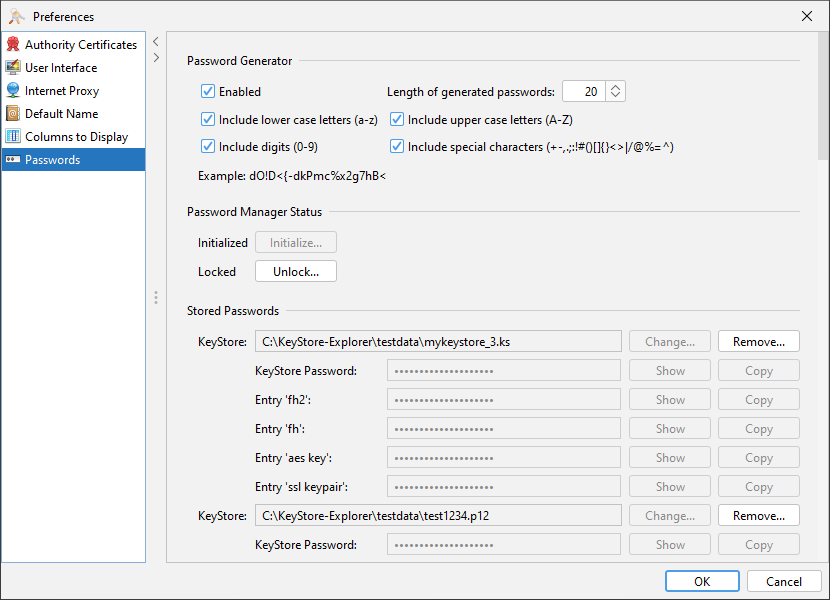
In the preferences dialog a new section has been added for the configuration of both the password manager and the password generator.
In the next releases, more configuration options for the password manager will be added.
Details about the password manager can be found in the documentation.
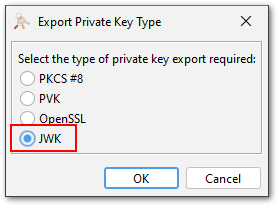
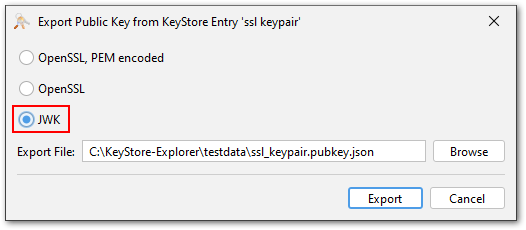
Key Export in JWK Format
The JSON Web Key (JWK) format is a JSON representation of cryptographic keys. It is defined in RFC 7517 and is used in many modern web applications.
KSE can now export public and private keys in JWK format. Supported are currently RSA and EC keys (no Ed25519).
This feature was contributed by tenpertur.
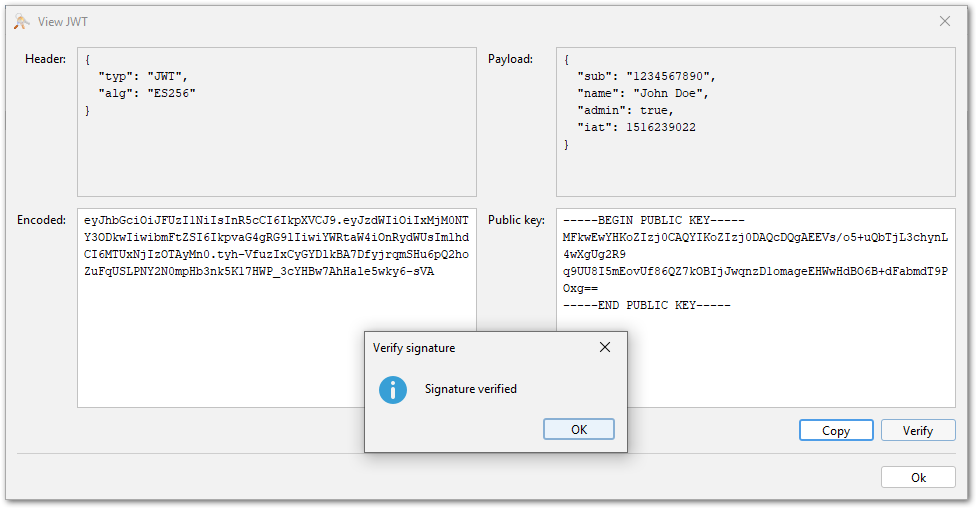
Verification of JWT Signatures
In one of the last releases, KSE introduced a viewer for JWT (JSON Web Token) files, which can be used via the "Examine File" or "Examine Clipboard" menu items.
This JWT viewer can now also verify the signatures of JWT files. This is done by pasting a public key in encoded as PEM or Base64 DER into the public key field of the JWT viewer and then clicking the verify button. Supported are RSA and EC keys and the corresponding signature algorithms ("RS...", "ES..." and "PS...").
This feature was contributed by Jairo Graterón.
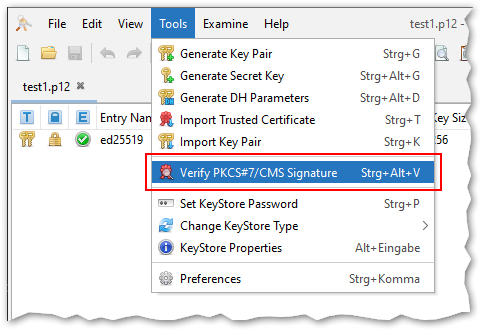
File signing and verification using PKCS#7/CMS
KSE now supports signing and verifying arbitrary files using PKCS#7/CMS. This is a widely used standard for signing files.
This feature can be found in the context menu of key pair entries:
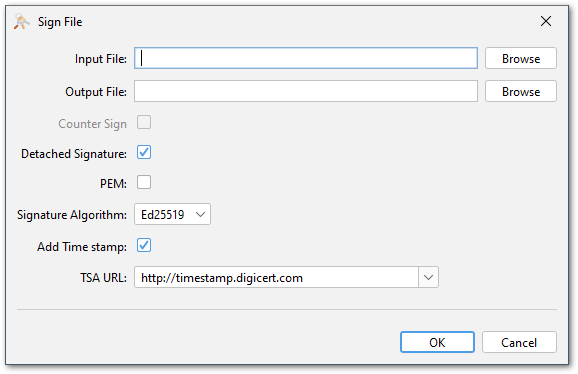
The PKCS#7 file can be either stored separately as a so-called "detached signature" or the signed file can be embedded in the PKCS#7 file. The latter is called "enveloped signature". In both cases the output format can be either PEM or binary DER.
A TSA (timestamp authority) can be used to timestamp the signature. KSE includes a list of well-known TSAs that can be used for this purpose. If you want to use another TSA, then its URL can be entered manually instead.
And finally the signature can be added as a "counter signature" to an existing PKCS#7 file. A counter signature does not sign data but another signature.
This feature was contributed by jonwltn.
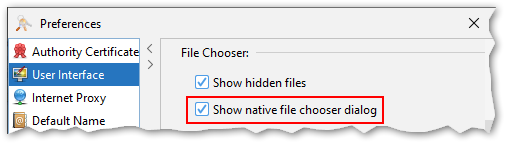
Native File Chooser
This is not really a new feature, but so far there have been several restrictions that prevented the native file chooser to be available in KSE for a majority of the users. First of all the Java runtime had to include the JavaFX library, which is not the case anymore for most modern Java distributions. Also, on macOS the native file chooser had to be disabled because of an incompatibility between tools like Karabiner or Cinch and the JavaFX library. This seems to be fixed now.
Starting with this release KSE includes the JavaFX library and the native file chooser can be enabled in the preferences.
New PKCS#12 Features
PKCS#12 is a very flexible format. It can contain an arbitrary number of key pairs, certificates and even CRLs. A wide range of encryption algorithms can be used to protect the contents of a PKCS#12 file.
With this flexibility comes complexity. There have always been compatibility issues with PKCS#12 files created by different tools. This situation has not exactly improved when Java 8 introduced support for so-called "trusted certificates" (i.e. standalone certificates that are not associated with a key in the same file) in PKCS#12 files by marking them with a custom bag attribute with OID "2.16.840.1.113894.746875.1.1".
As a result any certificate in a PKCS#12 file that is not part of the chain belonging to a key in the same file is simply ignored by the Java runtime. This has caused a lot of confusion among users.
In the meantime OpenSSL v3.2 has added a new flag "-jdktrust anyExtendedKeyUsage" to its pkcs12 command that allows to create PKCS#12 files with standalone certificates that are compatible with Java:
$ openssl pkcs12 \
-export \
-out test.p12 \
-in test.cer \
-jdktrust anyExtendedKeyUsage
$ keytool -list -keystore test.p12
Enter keystore password:
Keystore type: PKCS12
Keystore provider: SUN
Your keystore contains 1 entry
1, Jan 28, 2024, trustedCertEntry,
Certificate fingerprint (SHA-256): 52:68:B6:49:C9:8B:16:...
PKCS#12 Content Viewer
With OpenSSL, keytool and KSE being able to create and read PKCS#12 files with trusted certificates, there a few use cases left where KSE is not able to read certificates in PKCS#12 files created by other tools.
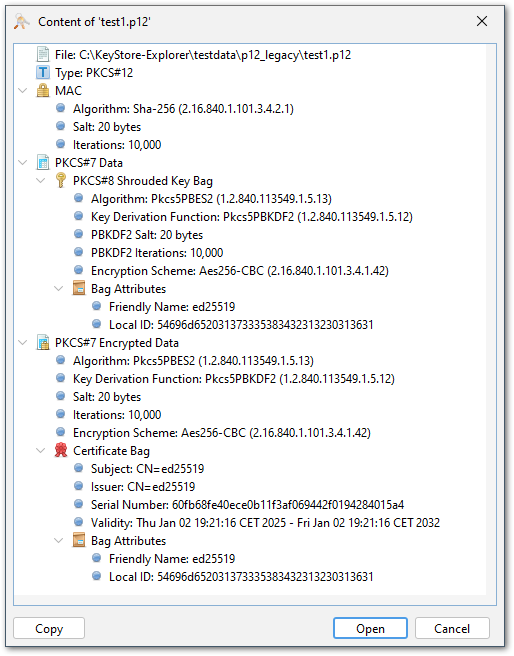
The new PKCS#12 viewer can be used to inspect the contents and structure of PKCS#12 files and help identify possible issues. The viewer can be opened via the "Examine File" or "Examine Clipboard" menu items. Also drag and drop of PKCS#12 files or opening them by double-clicking them in the file manager will open the PKCS#12 viewer first.
The p12 viewer shows the contents and structure of the PKCS#12 file in a tree view. The details of each entry can be viewed by expanding it in the tree view. The details include the type of the entry, the algorithm used to encrypt it and the parameters. Keys and certificates are not included, just some information like subject/issuer and serial number to identify them.
For p12 files that cause issues in KSE, the viewer might help to identify the cause of the problem. There is a "Copy" button that copies the visible structure as text to the clipboard. This then can be pasted into a GitHub issue to provide the developers with the necessary information to analyse the issue.
After inspecting the contents of the PKCS#12 file, it can be opened in KSE by clicking the "Open" button.
This feature is only temporary and will either be completely removed, reworked or moved to a less prominent place. But right now PKCS#12 is a very important topic and the viewer should help a lot with it.
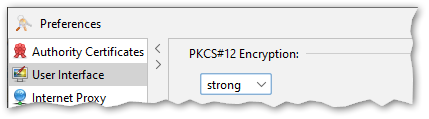
Reworked Encryption Settings for PKCS#12
The encryption settings for PKCS#12 files introduced in KSE v5.5.2 have been reworked. The previous implementation in some cases required a restart of KSE to take effect. The new implementation works reliably without a restart. Note that this setting is only used when creating a new PKCS#12 file.
Same Password for Whole PKCS#12 Content
Internally PKCS#12 files consist of "bags" that contain certificates or keys. Each key bag can be encrypted with a different password. This matches the KeyStore API which allows to use different passwords for each entry in a KeyStore. However, the widely established convention is to use the same password for all bags in a PKCS#12 file.
KSE now uses the same password for all entries when a PKCS#12 keystore is created or modified. When a PKCS#12 keystore is opened, KSE will try to use the keystore password for all entries. Only if this fails, KSE will ask for an entry password.
New Configuration System
In previous releases KSE used the Java Preferences API to store its configuration. This API is not very flexible and has some limitations. For example, it is difficult to store complex configuration objects. Also, the location of the configuration differs from platform to platform. On Windows it is stored in the registry, on macOS in a plist file and on Linux in a hidden directory in the home folder. This makes it difficult to share the configuration between different platforms or add a portable mode to KSE where the configuration files are stored in the same directory as KSE.
KSE now uses a custom configuration system that stores the configuration always in a file and searches for it in the following locations in this order:
- If a environment variable "KSE_CONFIG_DIR" is set, then this path is used.
- In the same directory as the KSE program files (kse.jar etc.)
- In a OS-specific configuration folder:
- Windows: %APPDATA%/kse/
- Linux and macOS: ~/.config/kse/
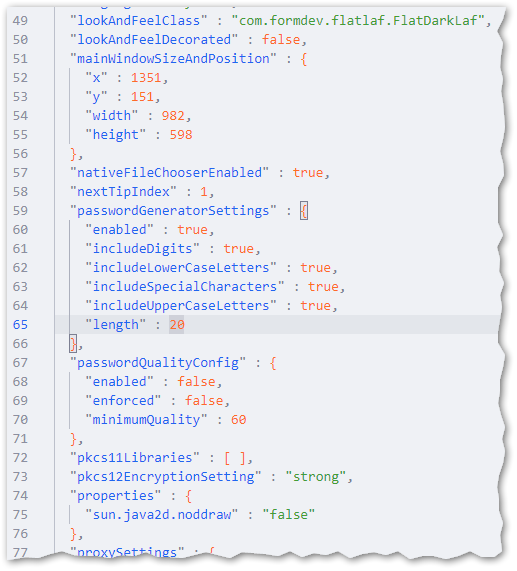
The configuration is stored in a JSON file called "config.json". The configuration file is created automatically after KSE was used for the first time.
The encrypted passwords of the password manager are stored in a separate file called "keystore-passwords.json". This file is stored in the same directory as the main configuration file.
The configuration file also includes now a section for system properties. This allows to set system properties like "sun.java2d.d3d.onscreen", which fixes a rare redraw issue on Windows. There is currently no GUI for this, because it is only needed for very special use cases.
There is no automatic migration of the old configuration to the new one.
Other Enhancements
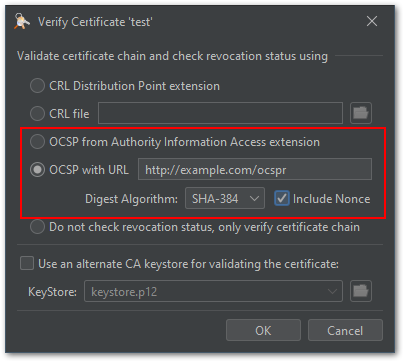
- The options for verifying a certificate have been extended to manually provide OCSP request parameters like:
- OCSP URL
- Hash algorithm
- Nonce request extension
Using the value from AIA extension instead is still possible.
This feature has been contributed by Erik Mattheis.
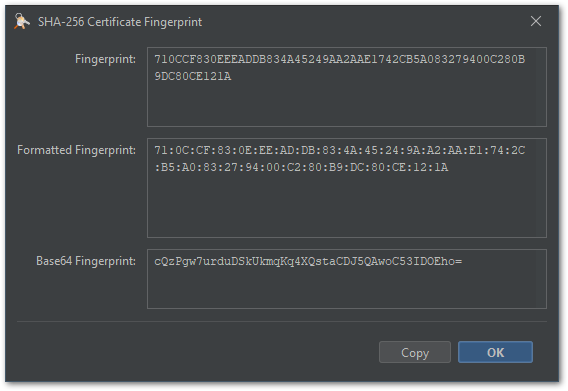
- The fingerprint views for certificate and public key fingerprints shows the value now in three different
formats:
- Hexadecimal
- Hexadecimal with a ":" as separator between the bytes
- Base64
This feature has been contributed by Jairo Graterón.
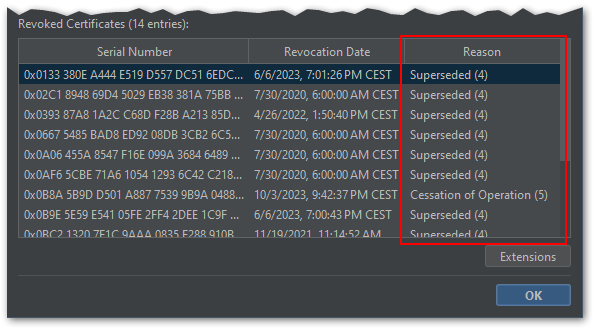
- The CRL viewer has been enhanced to show the revocation reason code. This feature has been contributed by jonwltn.
- Export of multiple certificates at once is now possible (contributed by Jairo Graterón)
- Added DESCRIPTION (OID 2.5.4.13) for DNs (contributed by Jairo Graterón)
- DH parameters are now displayed in a scrollable pane (contributed by Jairo Graterón)
- Additional file name extensions supported for "Examine Clipboard" and "Extension Viewer" (contributed by Jairo Graterón)
- Copy error message to clipboard (contributed by Jairo Graterón)
- "View Private Key" dialog now displays the original key format when examining a file or the clipboard (contributed by AndresQ)
- Improved usage of JavaFX file chooser in various ways (contributed by Colbix)
- Added keyboard support for context menu, either dedicated key or Shift-F10 (contributed by jonwltn)
- Support executing kse.sh with spaces in JAVA_OPTIONS (contributed by dadaewq)
- If the PQC algorithms that have been standardized by the NIST are used in certificates (either as signature or public key), they are now shown by their name
- Replaced Symantec's TSA with Microsoft's (due to termination of service)
- The Look&Feel can now be changed without a restart
- As a workaround for redraw issues with certain GPUs, the property "sun.java2d.d3d.onscreen" is now to "false". This can be changed - if necessary - by manually editing the config file (see above for its location and name).
Translations
- New translation: Spanish contributed by Jairo Graterón
- New translation: Russian contributed by Sergey Ponomarev
- New translation: Chinese contributed by liyansong2018
- Many additions and improvements of the French translation were contributed by The-Lum
Packaging
- macOS: Added native package for Apple Silicon (partially contributed by jonwltn)
- macOS: The Vaqua theme is not included in this release because of changes in Apple's notarization process: If jar files contain native libraries, these must be signed with an Apple developer certificate which is not the case for the Vaqua theme. If a solution is found for this problem, Vaqua will be included again in a future release of KSE.
- Linux: Added more MIME types to the kse.desktop files (contributed by Sergey Ponomarev)
- Linux: Fixed Debian package lint warnings (contributed by Sergey Ponomarev)
- macOS/Windows: Upgraded included Java runtime to version 21
- Java 11 is the new minimum runtime version
- Third-party libraries have been updated to their latest versions; BC is now at version 1.80
Bugfixes
- Fixed issue with very long OID arcs
- Fixed verify for SPKAC not working
- Fixed issue with organizationIdentifier name component
- Fixed missing curve name for non-BC EC private keys
- Fixed problem with UserNotice on CertificatePolicies extension
- Fixed restart issues
- Fixed issue with file filter when using JavaFX file chooser
- Fixed issue with switching between p12 legacy/strong encryption
Older Release Notes
KeyStore Explorer Release 5.5.0, 5.5.1, 5.5.2 and 5.5.3
KeyStore Explorer Release 5.4.0, 5.4.1, 5.4.2, 5.4.3 and 5.4.4
KeyStore Explorer Release 5.3.0, 5.3.1 and 5.3.2
KeyStore Explorer Release 5.2.0, 5.2.1 and 5.2.2
KeyStore Explorer Release 5.1.0 and 5.1.1
KeyStore Explorer Release 5.0.0 and 5.0.1