Release 5.2.2 27 Nov 2016
This release comes with another translation: German (contributed by Frank Dietrich).
It also includes the following bug fixes:
- Fixed problem that Java runtimes with three-digit version number (e.g. 8u101) were not found by the Windows launcher (kse.exe).
- Fixed authorityCertIssuer in AKI extension (patch contributed by Peter Breur).
- Fixed problem when generating EC keys with crypto devices (patch provided by Andreas Schwier).
- Ignoring unsupported certificate types now (patch provided by Andreas Schwier).
- Java 8 update 101 finally fixed a problem with duplicate aliases in MSCAPI keystore, which caused an exception in the workaround code in KSE when opening the Windows-MY keystore. The workaround code has been removed now from KSE (reported by Helmut Schulz).
- Fixed compatibility problems of jar signatures in combination with older Java versions (reported by dmacjr).
- Fixed problem with missing start menu entries in Windows 10 (reported by bennypi).
- Fixed last used PKCS#11 libraries not being stored in preferences (reported by Uri Blumenthal).
- Removal of crypto restrictions works again now.
The included Bouncy Castle library has been updated to version 1.55.
Release 5.2.1 13 Aug 2016
KeyStore Explorer 5.2.1 is a maintenance release. It includes fixes for the following issues:
- On Mac OS X opening a file froze KSE when there are other applications installed that use the accessability API (reported by ke5stl and Markus Rudel). As a workaround for this incompatibility the native file dialog has been removed for OS X.
- The shell script (kse.sh) didn't start through a symlink because it incorrectly detected its parent folder (fix contributed by Josef Ludvicek).
- NPE in NameConstraints extension when there is no max. value in excludedSubtrees (reported by Ruffin).
- After opening a MSCAPI or PKCS11 keystore, the restrictions for export etc. were applied to all other keystore types as well.
- ExamineFile/ExamineClipboard: When there were multiple concatenated PEM certs in one file, KSE showed only the first one.
- A very rarely occurring bug in JEditorPane's constructor caused exceptions on startup.
Release 5.2 15 May 2016
KeyStore Explorer version 5.2 is a huge feature release, adding more than 30 new features and enhancements.
It is the first version of KSE that can access hardware keystores like smart cards and hardware security modules (HSMs) using the PKCS#11 and MSCAPI providers.
New Feature: MSCAPI Keystore Type
Since Java 6 the SunMSCAPI provider is part of the JRE, enabling software written in Java to access the native cryptographic services and key containers of the Windows platform.
So far KSE only allowed to use "Windows-ROOT" as a truststore ("Preferences" -> "Authority Certificates").
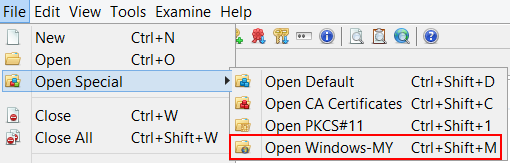
In KSE 5.2 you can now open the "Windows-MY" keystore (s. screenshot), which contains the user's personal certificates and associated private keys. This includes keys that are located on a smart card, as long as the matching middleware is installed.
Note that due to restrictions of the SunMSCAPI provider not all features are available, that would be available for other keystore types.
New Feature: PKCS#11 Keystore Type
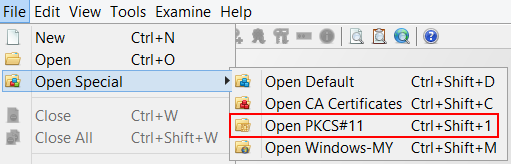
PKCS#11 is a standard that defines an API for accessing cryptographic devices. In Java the SunPKCS11 provider wraps the PKCS#11 API and transforms it into the keystore API.
There are two ways to use a PKCS#11 library in KSE:
- Add the SunPKCS11 provider to the Java Security properties file. This is described in detail in the Java PKCS#11 Reference Guide and also often in the documentation of the cryptographic device. You can then simply select it in KSE in the "Open PKCS#11 KeyStore" dialog.
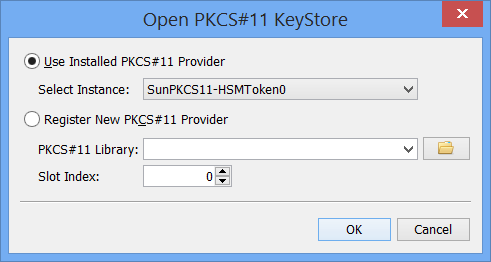
- Alternatively, KSE can register the SunPKCS11 provider itself, if you provide the path to the PKCS#11 library and the right slot index.
Note that because PKCS#11 libraries are native code you have to make sure that both the JRE and the PKCS#11 library are either 32 or 64 bit.
The combination of SunPKCS11 provider, middleware and hardware often does not work very well together: Sometimes the token can be opened, but not be used for signing, sometimes not even opening the token works. As a rule of thumb, if it works with keytool/jarsigner, then it should work with KSE as well. Please avoid opening bug reports about device xy not working in KSE. It's only a bug if it works in keytool/jarsigner but not in KSE.
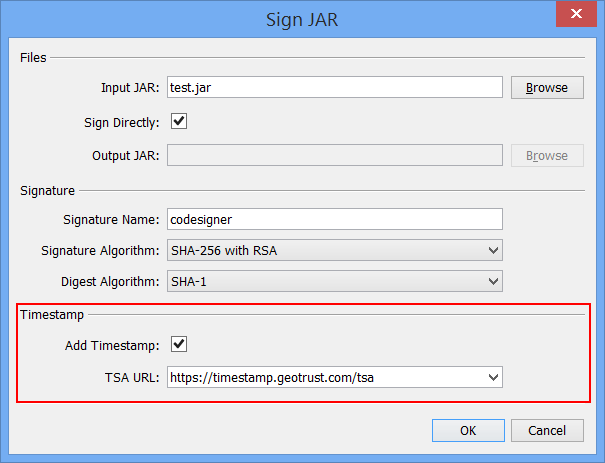
New Feature: Timestamping Jar Signatures
KSE can now generate and store a signature timestamp when signing a JAR file. All you have to do is select the option "Add Timestamp" in the sign jar dialog and choose a Time Stamping Authority (TSA) from a list (or enter the URL of another TSA).
The following URLs of TSAs are pre-defined:
- https://timestamp.geotrust.com/tsa
- http://tsa.starfieldtech.com
- http://www.startssl.com/timestamp
- http://timestamp.globalsign.com/scripts/timstamp.dll
- http://timestamp.comodoca.com/rfc3161
KSE communicates with the TSA using the Time-Stamp Protocol (TSP) defined in RFC 3161. The timestamp token returned by the TSA is stored along with the signature in the signature block file.
Improved Extension Viewer
The certificate extension viewer has been vastly improved. Almost 40 additional extensions are recognized:
- RFC 3739 QC private extensions: BiometricInfo (1.3.6.1.5.5.7.1.2), QCStatements (1.3.6.1.5.5.7.1.3)
- RFC 2560 private extensions: OCSPNoCheck (1.3.6.1.5.5.7.48.1.5)
- Common PKI 2.0: LiabilityLimitationFlag (0.2.262.1.10.12.0), DateOfCertGen (1.3.36.8.3.1), Procuration (1.3.36.8.3.2), Admission (1.3.36.8.3.3), MonetaryLimit (1.3.36.8.3.4), DeclarationOfMajority (1.3.36.8.3.5), ICCSN (1.3.36.8.3.5), Restriction (1.3.36.8.3.8), AdditionalInformation (1.3.36.8.3.15)
- Microsoft: MSEnrollCerttypeExtension (1.3.6.1.4.1.311.20.2), MSCaVersion (1.3.6.1.4.1.311.21.1), MSCACertificateHash (1.3.6.1.4.1.311.21.2), MSCRLNextPublish (1.3.6.1.4.1.311.21.4), MSCertificateTemplate (1.3.6.1.4.1.311.21.7), MSApplicationPolicies (1.3.6.1.4.1.311.21.10)
- RFC 3851: SMIMECapabilities (1.2.840.113549.1.9.15)
- RFC 3709: LogoType (1.3.6.1.5.5.7.1.12)
- CDC (TU Darmstadt): ValidityModel (1.3.6.1.4.1.8301.3.5)
- SET (Secure Electronic Transaction): SETHashedRootKey (2.23.42.7.0), SETCertificateType (2.23.42.7.1), SETMerchantData (2.23.42.7.2), SETCardCertRequired (2.23.42.7.3), SETTunneling (2.23.42.7.4), SETSetExtensions (2.23.42.7.5), SETSetQualifier (2.23.42.7.6)
- VeriSign: VeriSignCZAG (2.16.840.1.113733.1.6.3), VeriSignNonVerified (2.16.840.1.113733.1.6.4), VeriSignFidelityToken (2.16.840.1.113733.1.6.5), VeriSignInBoxV1 (2.16.840.1.113733.1.6.6), VeriSignSerialNumberRollover (2.16.840.1.113733.1.6.7), VeriSignTokenType (2.16.840.1.113733.1.6.8), VeriSignNetscapeInBoxV2 (2.16.840.1.113733.1.6.10), VeriSignOnSiteJurisdictionHash (2.16.840.1.113733.1.6.11), VeriSignUnknown (2.16.840.1.113733.1.6.13), VeriSignDnbDunsNumber (2.16.840.1.113733.1.6.15)
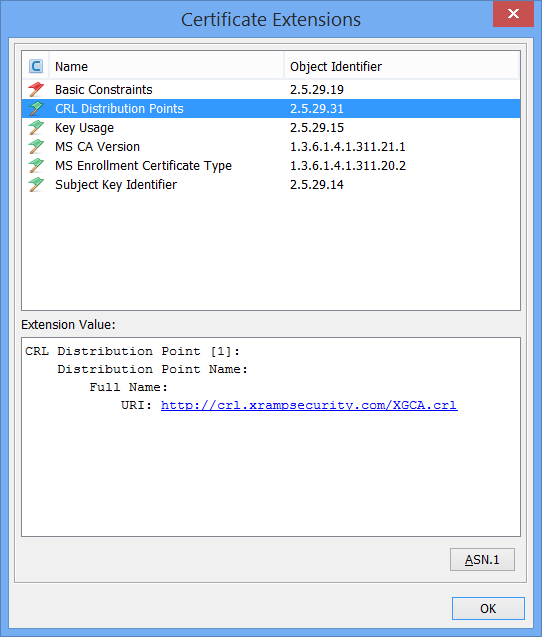
The following additional extended key usages (EKUs) are now recognized as well:
- DocumentSigningExtKeyUsage (1.3.6.1.4.1.311.10.3.12)
- AdobePDFSigningExtKeyUsage (1.2.840.113583.1.1.5)
- EncryptedFileSystemExtKeyUsage (1.3.6.1.4.1.311.10.3.4)
- SmartcardLogonExtKeyUsage (1.3.6.1.4.1.311.20.2.2)
- AnyExtendedKeyUsageExtKeyUsage (2.5.29.37.0)
- MicrosoftSGCExtKeyUsage (1.3.6.1.4.1.311.10.3.3)
- NetscapeSGCExtKeyUsage (2.16.840.1.113730.4.1)
- VeriSignSGCExtKeyUsage (2.16.840.1.113733.1.8.1)
URLs in extensions (like CDP or CPS) are now clickable. Linked certificates or CRLs are shown right in KSE. Other URLs are opened in the browser.
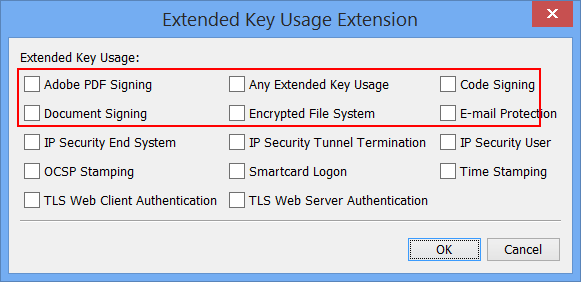
Additional ExtendedKeyUsage Types for Certificate Generation
Five additional types can now be added to the ExtendedKeyUsage (EKU) extension.
These are:
| Name | OID |
|---|---|
| DocumentSigningExtKeyUsage | 1.3.6.1.4.1.311.10.3.12 |
| AdobePDFSigningExtKeyUsage | 1.2.840.113583.1.1.5 |
| EncryptedFileSystemExtKeyUsage | 1.3.6.1.4.1.311.10.3.4 |
| SmartcardLogonExtKeyUsage | 1.3.6.1.4.1.311.20.2.2 |
| AnyExtendedKeyUsageExtKeyUsage | 2.5.29.37.0 |
This is a user contribution by Uri Blumenthal.
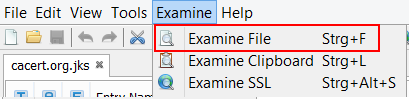
Examine File
The three previously separate features "Examine Certificate", "Examine CSR" and "Examine CRL" have been combined into "Examine File". KSE detects the content of the file and opens it if it is certificate, a CSR, a CRL or a keystore.
System Clipboard Integration
Sometimes you have a PEM encoded certificate or CSR in a mail, on a website or in a larger text document and want to see the content. Normally this means to copy the lines into a new text file, save it somewhere on the hard disk and then open the file with KSE or another certificate viewer. It would be so much easier to directly open the certificate from the clipboard. That's what "Examine Clipboard" does.
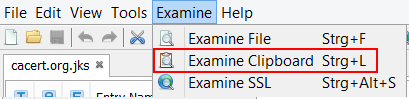
If you have transmitted a CSR and the CA shows the issued certificate in PEM format on its website or sends it in PEM format in an email, then you can simply copy it and use the new "Import CA reply from Clipboard" feature.
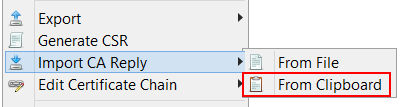
New Option: Use System Proxy Settings
In previous versions of KSE it was necessary to enter the proxy configuration manually. KSE 5.2 can now detect and use the proxy settings of the operating system, which should work in most cases.
This is the new default setting.
New Look&Feel: Darcula
Darcula is the nice dark L&F of IntelliJ IDEA. It has been made available by the developer as a separate project on GitHub.
Unfortunately it is an older version, which is not suited for high DPI displays. If you have one of those, it might help to add a comment here.
French Translation
The first translation of KSE was contributed by Davy Defaud.
Other Enhancements
- Switched to Oracle's PKCS#12 Implementation because it is more reliable and fits better in the keystore model. This fixes several bugs. The key passwords, which were previously hidden because they are set to the same value as they keystore password, are now unveiled.
- Added automatic update check
- Added IPv6 addresses for SubjAltName (contributed by Chris Ridd)
- Support viewing of non-CRT RSA private key fields (contributed by Chris Kistner)
- Added otherName UPN as an option for SubjectAlternativeName extension
- Native file dialogs where JavaFX is available (usually Java 8 and higher)
- Installing the JCE Unlimited Crypto Strength policy is no longer necessary (contributed by Kevin Herron)
- Added retry on password error
- KSE now opens certificates, CRLs and CSRs that were passed as command line parameters
- Default LaF for Linux is now GTK+ (if available)
- Localized date format
- Trying default password ('changeit') first now when opening cacerts (before asking the user)
- Added bigger application icons (256x256 and 512x512) to the ZIP package
- Added credits button to about dialog; moved system infos to help menu
- Preferences node moved to /org/kse
- Added check for existence of configured cacerts file
- Added a SPEC file to the sources to build an RPM (contributed by Davy Defaud)
- Accepting the license is no longer required to install/run KSE
- Path for GenerateCSR file name suggestion is now generated from keystore path
- New default setting for both trust checks (import CA reply and import trusted cert) is false
Bug Fixes
- Fixed problems with SNI (Examine SSL)
- Fixed Authority Key Identity extension (contributed by Filip Jirsák)
- Fixed application name in Gnome 3 top bar
- Fixed some issues with high DPI displays
- Fixed bugs in GeneralNames editor (reported by devdas77)
- Fixed secret (symmetric) keys not being available for BKS-V1
Older Release Notes
KeyStore Explorer Release 5.1.0 and 5.1.1
KeyStore Explorer Release 5.0.0 and 5.0.1