Release 5.4.4 4 Oct 2020
This release includes the following improvements and bug fixes:
- Certificate serial numbers can now be entered in hexadecimal format as well (contributed by Stephen Tomkinson). Hex numbers are detected ...
- if the input contains the letters a-f or A-F, for example "1a2b3c4d5e6f" or "1A2B3C4D5E6F" (decimal: 28772997619311)
- or if the input starts with "0x", for example "0x12345678" would be interpreted as decimal 305419896
- Additional button in "Certificate Extensions" window to save those extensions as a template (contributed by Stephen Tomkinson)
- KSE allows now to select multiple entries by pressing SHIFT or CTRL and perform the following operations on all selected entries (contributed by Christoph Kaser):
- cut
- copy
- paste
- delete
- Fixed AKI/SKI extensions and Issuer/Subject Organisation not shown in table view (reported by Michael Karnerfors)
- Fixed AKI/SKI extensions not being updated when added from a template or CSR (reported by Michael Karnerfors)
- Fixed an error when inspecting a SAN extension that contains a User Principal Name (reported by e4711s)
- Key Usage extension is now correctly marked as critical in all default extension templates (reported by James K Polk)
- macOS: Fixed an incompatibility with VAqua Look&Feel that caused a save dialog to be shown instead of an open dialog (reported by Filipe Forneck, fix contributed by Gary Bartlett)
- macOS: VAqua Look&Feel is no longer the default
- macOS: The application bundle now contains a custom Java runtime. This fixes issues with detection of JRE installations and notarization.
- SHA256 is now used in timestamp requests (instead of SHA1)
- PKCS#12 is now the default when creating a new keystore. This reflects the transition from JKS to PKCS#12 as the default keystore in Java 9 (JEP 229).
- Updated Bouncy Castle library to version 1.66


Release 5.4.3 8 Mar 2020
This release includes the following bug fixes and improvements:
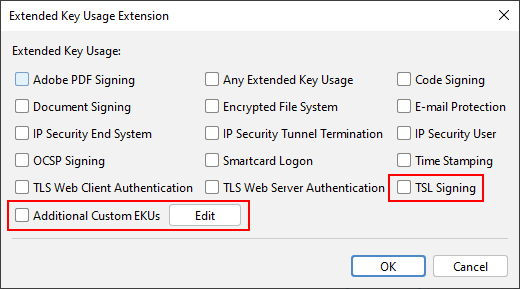
- Added support for custom extended key usages (contributed by Jordi Pinzón García)
- Added TSL (Trust-service Status Lists) signing extended key usage, OID "0.4.0.2231.3.0" (contributed by Vakhtang Laluashvili)
- After a keystore entry was deleted, the next entry is selected now. This makes deleteting several entries easier.
- JKS and JCEKS keystores can now be opened without entering the password, just press enter in the password dialog.
- This is only possible because the JKS/JCEKS keystore password (in contrast to the passwords of individual key entries) is just an integrity protection.
- Key entries are of course still locked.
- The keystore is handled by KSE as if no keystore password was set yet. If you want to save the keystore after a modification, you have to set a new keystore password.
- New Look&Feel for macOS: VAqua (contributed by Lothar Haeger)
- New Look&Feel for all platforms: FlatLaf (see screenshot to the right)
- Removed Look&Feel Darcula and JGoodies
- User manual is now part of the KSE website and was removed from the application.
- Fixed some smaller problems with German translation
- Updated Bouncy Castle library to 1.64
Release 5.4.2 11 Aug 2019
This release includes the following bug fixes and improvements:
- Certificate generation: Editing of extensions fixed (contributed by JPinzon01)
- Fixed date/time spinners and added shortcut buttons (contributed by Michele Mariotti)
- Fixed typos in German translation (contributed by Markus Stein)
- Fixed standard templates not working
- Fixed typo in EtsiQcsQcPDS in ASN.1 viewer (reported by weddi-eddy)
- Fixed issue in extension viewer when an unknown extension is encountered (reported by Daniel Mota Leite and hoogenpi)
- Added OID for RFC 6962 "Certificate Transparency"
- Allowing secret keys for keystore type PKCS#12 (requested by Laurent Vaills)
- Fixed cancel on extension template dialog when deleting current extensions
- Added release field to RPM (requested by gpavinteractiv)
- EC keys in PEM format with "-----BEGIN EC PARAMETERS-----" are processed now (EC parameters are ignored though)
- Fixed naming of ExtKeyUsage "OCSP Signing" (1.3.6.1.5.5.7.3.9)
- Fixed german translation of OCSP signing
- Fixed import of EC key in OpenSSL format not working (reported by mattes)
- "Add certificate extensions to CSR" is now enabled by default
- Updated included Bouncy Castle library to version 1.62
- Updated appbundler to latest version (fixes problems with alternative Java runtimes under macOS)
- Minimum required Java version for running KSE is now 1.8
Release 5.4.1 27 Oct 2018
This release includes the following bug fixes:
- Mac OS version: The Java Runtime Environment was not always found by the app bundle (reported by Gary Bartlett).
- Fixed unlimited strength policy file not recognized (reported by basuradeluis and Ralf Hauser).
- Fixed error when trying to view the "Policy Constraints" extension (reported by Robert W. Baumgartner).
- Fixed error when trying to view the "Subject Directory Attributes" extension (reported by Robert W. Baumgartner).
- Mac OS version: Removed version number from bundle identifier (reported by Core Code).
Release 5.4.0 20 Sep 2018
This release includes the following new features, enhancements and bugfixes:
Updated Preferences Dialog
Configurable Columns
In previous versions KSE showed a fixed set of information for keystore entries: Entry name, algorithm, key size, certificate expiration date and last modification date. If you wanted to find for example a certificate with a specific issuer DN the you would have to open every certificate in the keystore.
KSE 5.4.0 allows to freely configure the displayed columns. New fields are:
- Curve (for EC keys)
- Subject/Authority Key Identifier
- Subject/Issuer DN
- Subject/Issuer Organisation
- Subject/Issuer CN
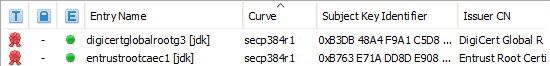
Also, certificates that are going to expire in the next n days can now be marked.
This feature was contributed by Wim Ton.
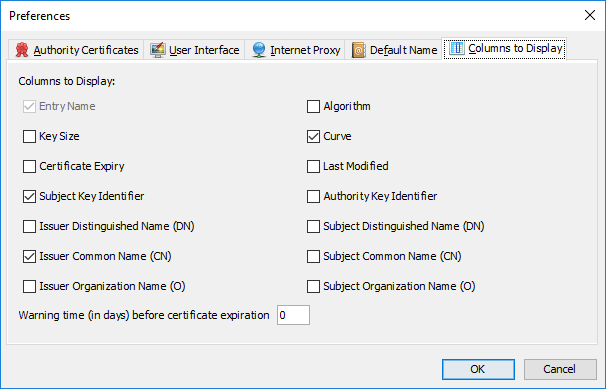
New Settings for UI Language and Automatic Update Checks
In previous versions KSE always used the system language for its UI (if there was a translation for it). Now you can explicitly choose between:
- System Language
- English
- French
- German
The automatic update check queries the KSE website for new releases of KSE and displays a notification if one was found. Starting with KSE 5.4.0 you can enable/disable automatic update checks and set an interval for them.
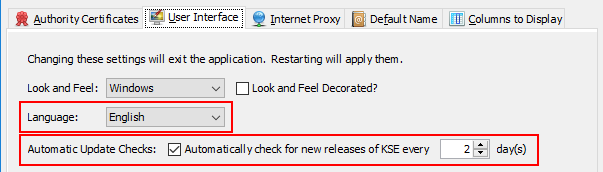
Improved CSR Generation and Signing
Edit Subject When Generating a CSR
In previous versions the subject name for a CSR was taken from the certificate of the selected key pair entry. This might not always be what you want. Therefore the subject is now editable.
Edit Subject When Signing a CSR
When signing a certificate for the public key from a CSR, the subject DN of the certificate is now freely editable. The subject name from the CSR is only used as a suggestion.
Transfer Extensions from CSR to Certificate
It is possible to add certificate extensions to a CSR. KSE can now transfer those extensions to the certificate. Every single extension from the CSR can then be edited or removed and additional extensions can be added.
View Additional Information About CSR
The "Sign CSR" dialog can now show more details about the CSR. Namely:
- The extensions included in the CSR.
- An ASN.1 dump of the CSR.
- The CSR in PEM format.
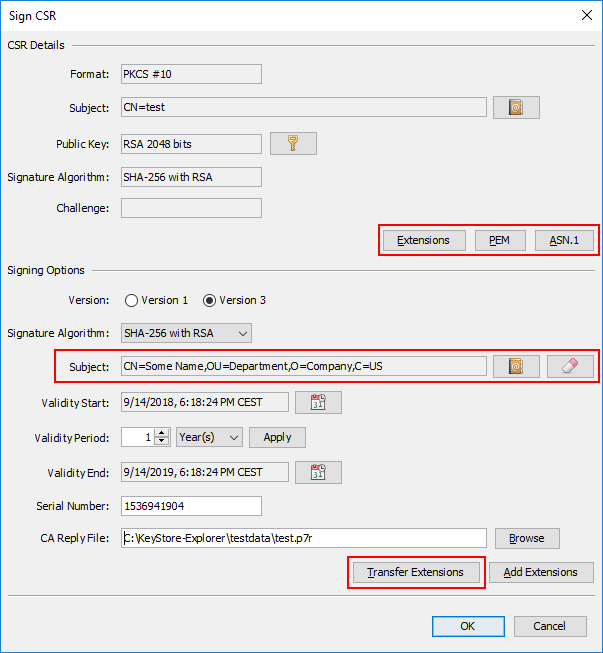
Pre-Defined Certificate Extension Templates
When generating a certificate it is a relatively cumbersome task to add all the extensions one by one. With this new feature you can add a basic set of commonly used extensions for four different certificate types.
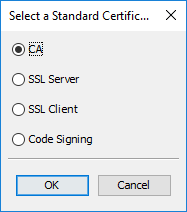
The pre-defined extension templates are:
| Template | Extensions |
|---|---|
| Certificate Authority |
Authority Key Identifier Subject Key Identifier Basic Constraints: CA=true Key Usage: Certificate Sign, CRL Sign |
| TLS/SSL Server |
Authority Key Identifier Subject Key Identifier Key Usage: Digital Signature, Key Encipherment Ext. Key Usage: Server Authentication |
| TLS/SSL Client |
Authority Key Identifier Subject Key Identifier Key Usage: Digital Signature, Key Encipherment Ext. Key Usage: Client Authentication |
| Code Signing |
Authority Key Identifier Subject Key Identifier Key Usage: Digital Signature Ext. Key Usage: Code Signing |
After selecting an extension template, additional extensions can be added. The extensions from the template can be edited or removed.
Note that these template sets are not necessarily complete, they are rather a starting point (which might be sufficient for some purposes). For example a TLS/SSL server certificate should also contain a Subject Alternative Name (SAN) extension with the site name in it.
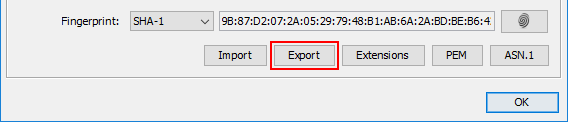
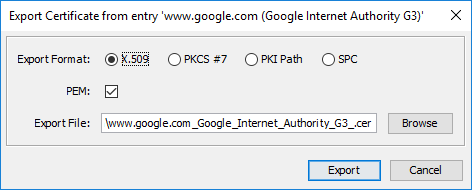
Export Button in Certificate Details Dialog
When opening a certificate with one of the following methods, it is now possible to save that certificate to the file system:
- Examine File (Ctrl-F)
- Examine Clipboard (Ctrl-L)
- Examine TLS/SSL (Ctrl-Alt-S)
This is for example useful for ...
- downloading a HTTPS certificate
- converting a certificate from PKCS#7/DER/PEM/SPC to PKCS#7/DER/PEM/SPC format
- saving a certificate that you got as PEM in an email as a DER encoded file (after viewing it with "Examine Clipboard")
This is a user contribution by Benny Prange.
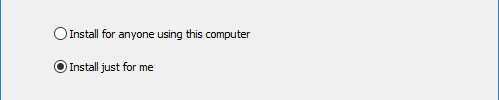
Multi-User Option for Windows Installer
The windows installer has now the option to install KSE for all users instead of only for the current user. This is especially useful for software deployment tools that run as system user.
This option is available in the installer GUI and as a command line parameter ("/AllUsers"). The default is
to install as current user.
BCFKS KeyStore Type
KSE has now support for Bouncy Castle's BCFKS keystore type. This includes the following operations:
- Create a new BCFKS keystore
- Open a BCFKS keystore
- Change keystore type from/to BCFKS
This feature was contributed by Kable Wilmoth.
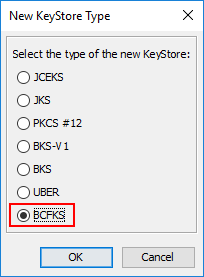
View Private/Public Keys as PEM
The "Private Key Details" and "Public Key Details" dialogs have now a new button "PEM", that shows the key in PEM format. It can be copied to system clipboard or saved to file system from there.
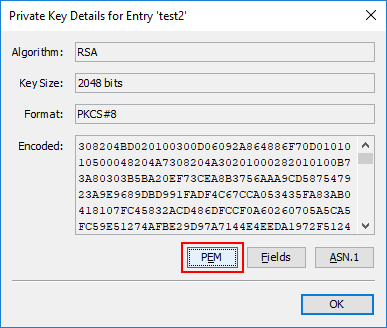
Change Value of Secret Key
The text field in the details dialog of secret (i.e. symmetric) key entries is now editable. This allows to replace an existing symmetric key in a keystore with another one.
Allowed format:
- Hex string ("2DF588C4280D...")
- No "0x" allowed
- Number of characters has to be even
- Upper/lower case does not matter: "2DF588C4280D..." or "2df588c4280d..." works
- Whitespace is ignored: "2D F5 88 C4 28 0D ..." works
- Colons (":") are ignored: "2D:F5:88:C4:28:0D ..." works
There are no explicit checks of the key value itself (e.g. no length checks or checks for parity bits in TDES keys).
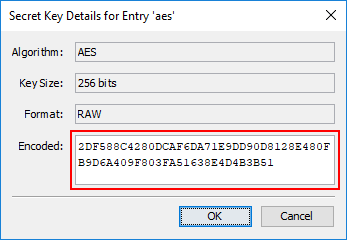
Updated List of Time Stamping Authorities
KSE can generate and store a timestamp when signing a JAR file. You can either enter the URL of a Time Stamping Authority (TSA) or select one from a list. Those URLs can change from time to time, therefore the list has been updated.
The updated list of TSAs is:
- http://timestamp.digicert.com
- http://timestamp.globalsign.com/scripts/timstamp.dll
- http://tsa.starfieldtech.com
- http://time.certum.pl
- http://sha256timestamp.ws.symantec.com/sha256/timestamp
- http://timestamp.comodoca.com/?td=sha25
Other Enhancements
- Added UID to DN chooser (contributed by Ha Nguyen)
- New shortcut "F2" for "rename entry"
- Focus in alias/password/DNchooser dialog is now on text
- Removed version from Windows installation directory name
- Made field for key data in details dialogs bigger
- Also accept private/public key files for examining/dnd
- Export key pair and certificate chain in one file in PEM format
- Windows launcher (kse.exe) compatible with Java 10/11 now
- KSE packages for Linux distributions in rpm and deb format
- Updated included Bouncy Castle library to 1.60
Bugfixes
- Fixed error in German translation (contributed by Benny Prange)
- Fixed permissions of kse.sh in zip file (contributed by Todd Kaufmann)
- Fixed "Other Name: UPN=" shown twice in extension editor (reported by Sivasubramaniam S MediumOne)
- Fixed illegal option error in kse.sh on macOS (reported by Venkateswara Venkatraman Prasanna)
- Fixed export of EC private key to OpenSSL format (reported by bsmith-tridium-com)
- Fixed missing leading zeroes in certificate fingerprint (reported by UltraChill)
- Fixed NPE when QC statement type is unknown and no statement info
- Fixed encoding of ECPrivateKey (RFC 5915) for OpenSSL format
- Fixed problem when loading EC public key file in OpenSSL format
- Fixed loading of OpenSSL format EC private key files
- Fixed: An empty key password was set when dragging and dropping a key pair entry
Older Release Notes
KeyStore Explorer Release 5.3.0, 5.3.1 and 5.3.2
KeyStore Explorer Release 5.2.0, 5.2.1 and 5.2.2
KeyStore Explorer Release 5.1.0 and 5.1.1
KeyStore Explorer Release 5.0.0 and 5.0.1